ICPSS Lecture Notes - Lesson 3 - Background
Networking
- Computer network connects two or more computing devices of the same or differing types
Types of networks
- Types of networks are categorized by the geographic area they cover
- BAN - body area network – local to a human body
- LAN - local area network – about building sized
- MAN - metropolitan area network – about city-sized, often falls between LAN and WAN and not a common term
- WAN - wide area network - global or regional, such as the internet
Network Topology
- The way in which devices are connected to a network
- Layout and paths
- Common topologies include:
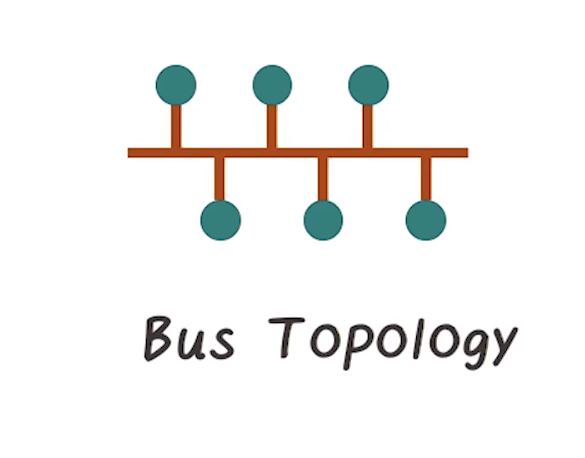
- Bus topology
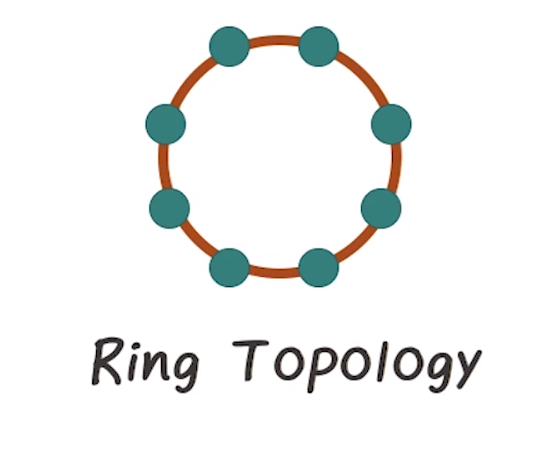
- Ring topology
- Star topology
- Extended star topology

- central nodes are backbone switches, directing traffic where it is needed
- Mesh topology

- used primarily for redundancy and fault tolerance
- also often used for wireless networks due to the nature of wireless as a medium
- Bus topology
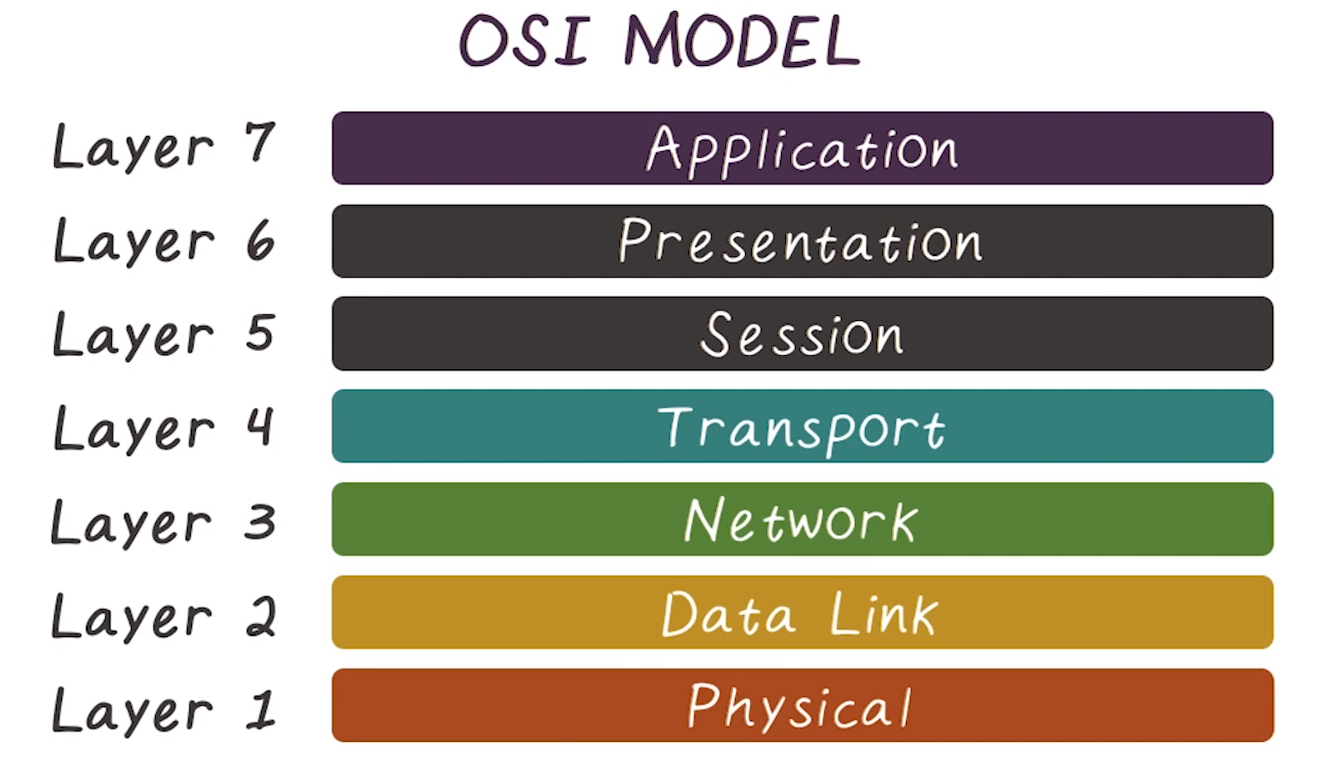
OSI Model
- Open Systems Interconnection
- Multiple protocols at each layer
- Owned by ISO (International Standards Organization)
- Each Layer serves a separate role
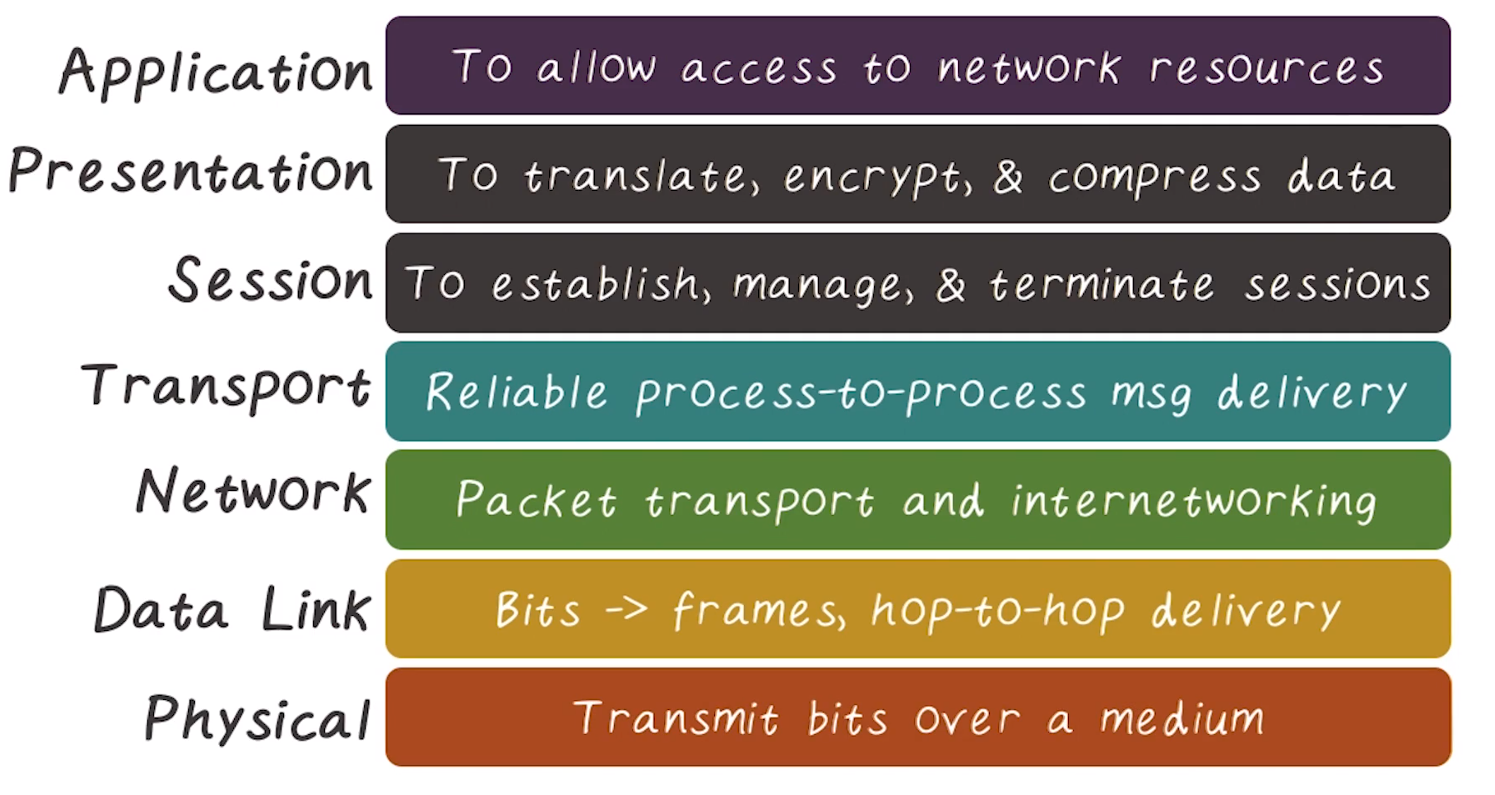
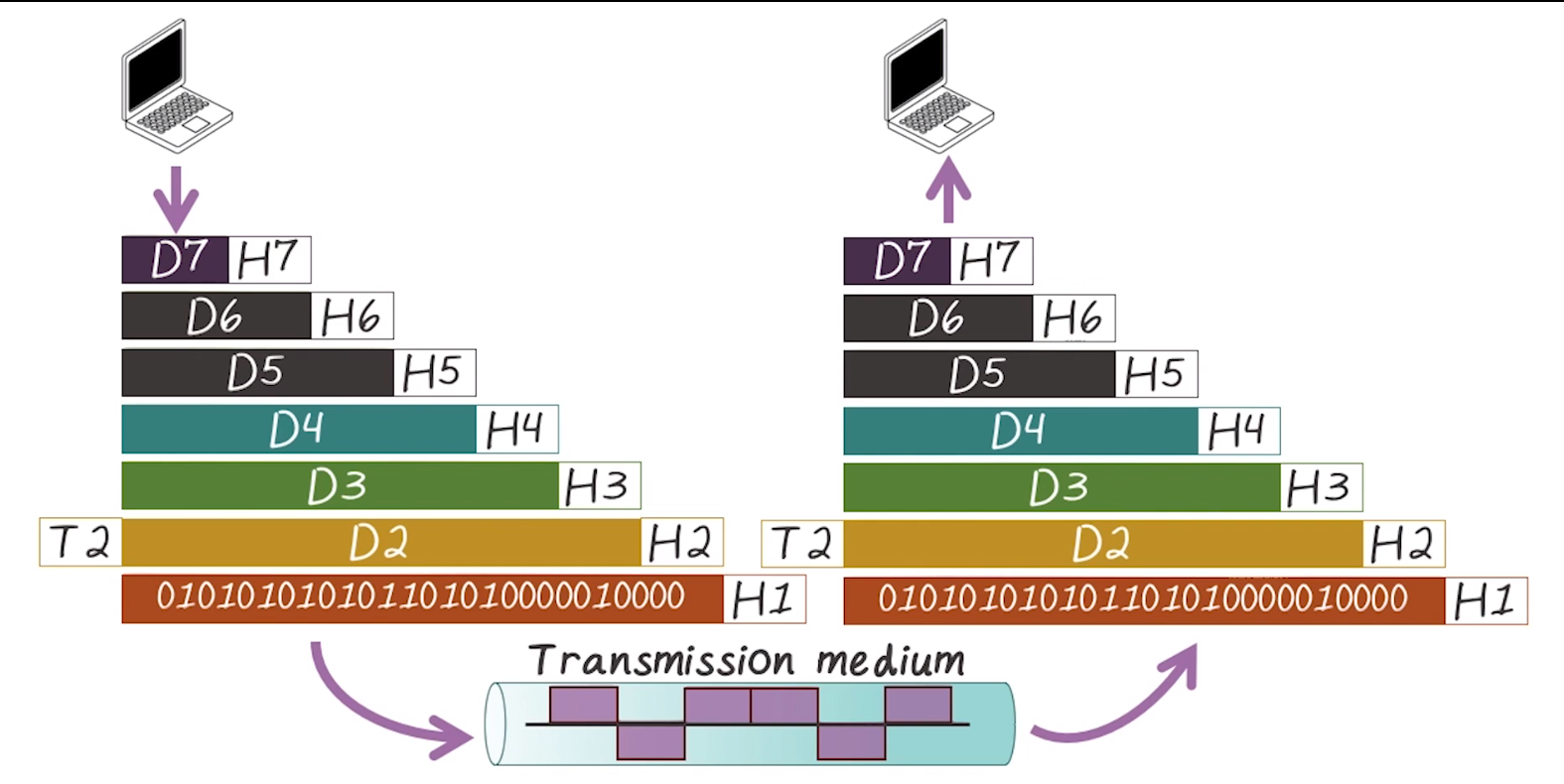
- Within a computer each layer uses the services of the layer below it
- Across computers, each layer communicates with the equivalent layer on the other machine
- It does this by traversing down the layer stack, and back up in the other machine
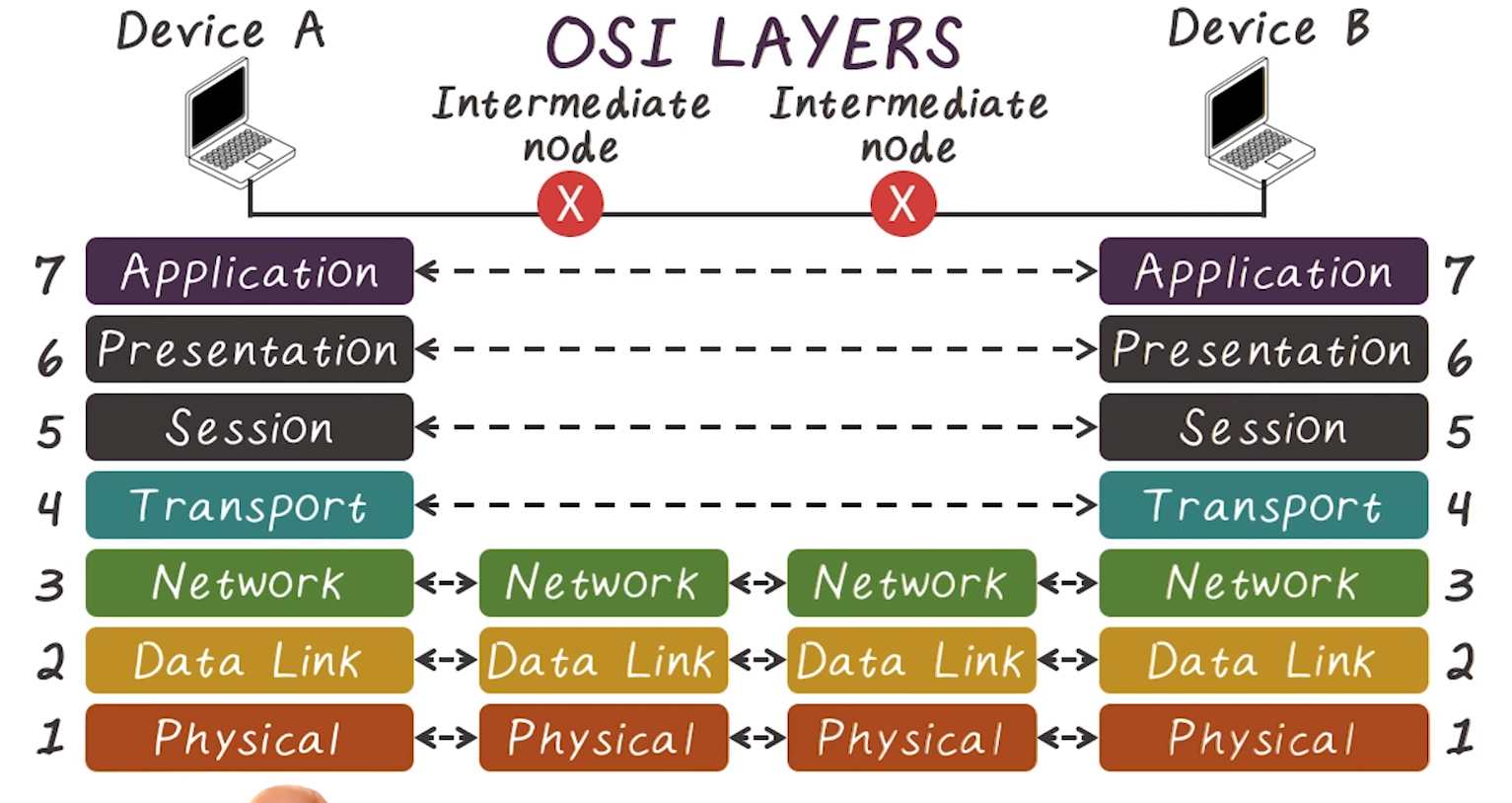
- Differentiates between end-to-tend layer and hop-by-hop layers, indicated in this diagram
- As information traverses down the stack, a header is added by each layer, and is stripped as it traverses back up.
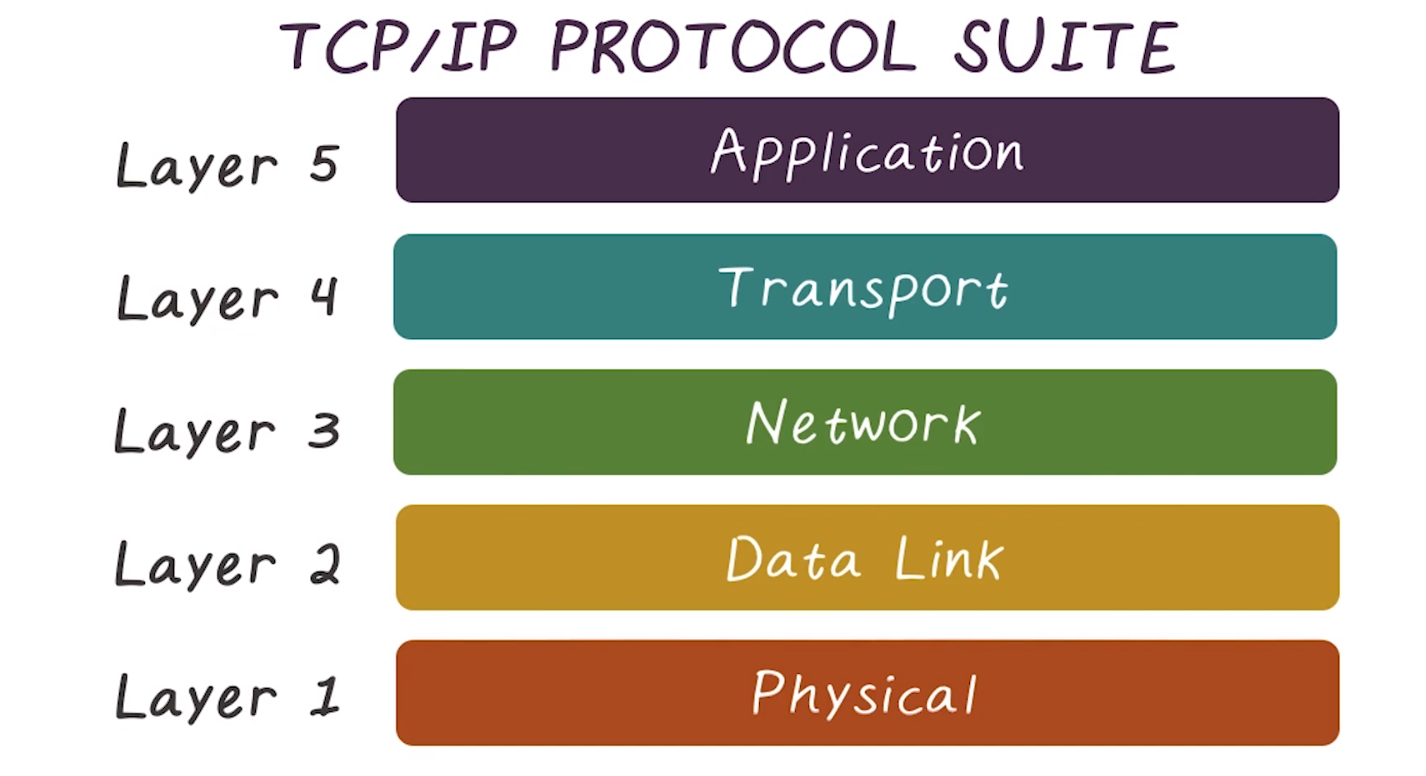
TCP/IP Protocol Suite
- developed before the OSI model, is similar but doesn’t quite line up
- Is generally more appropriate/accurate to actual protocol usage
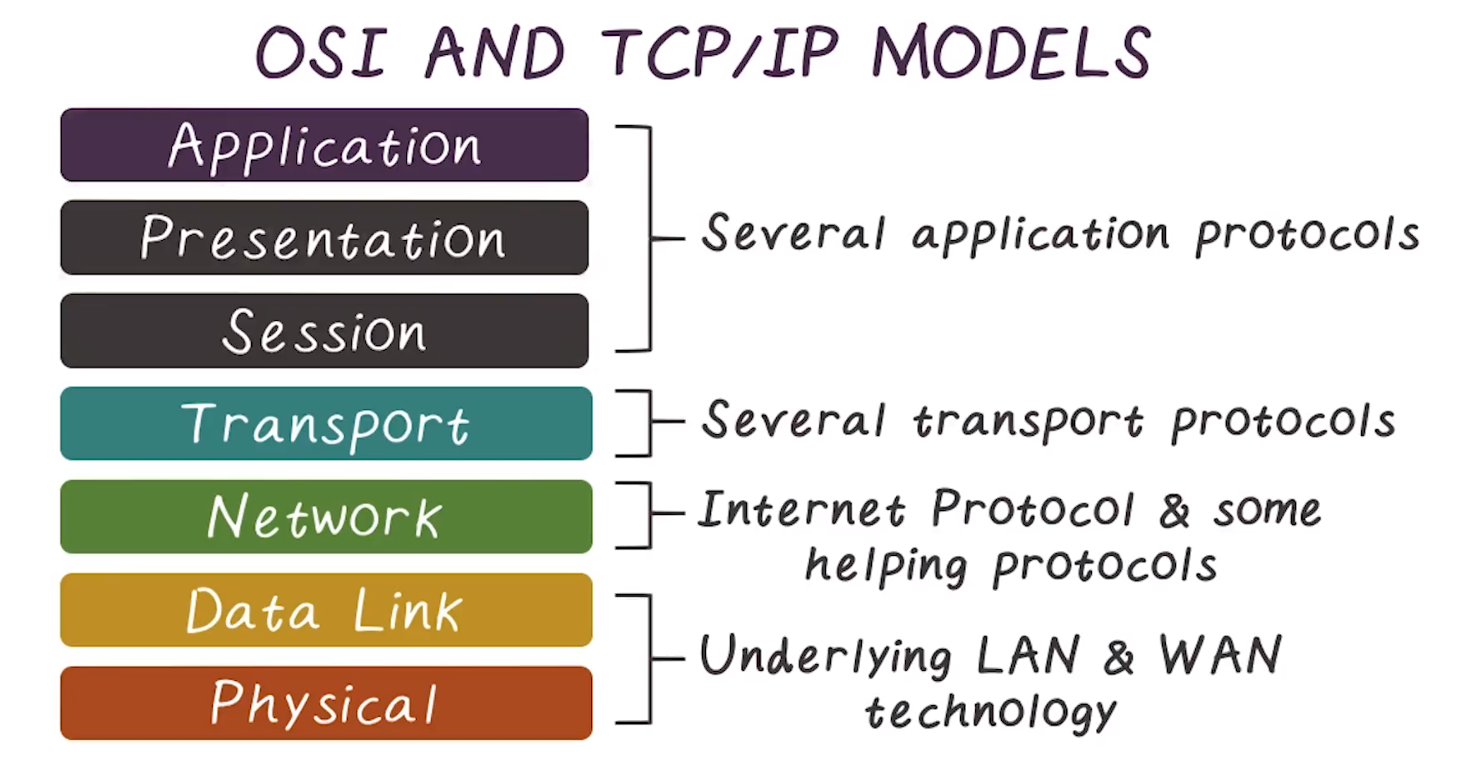
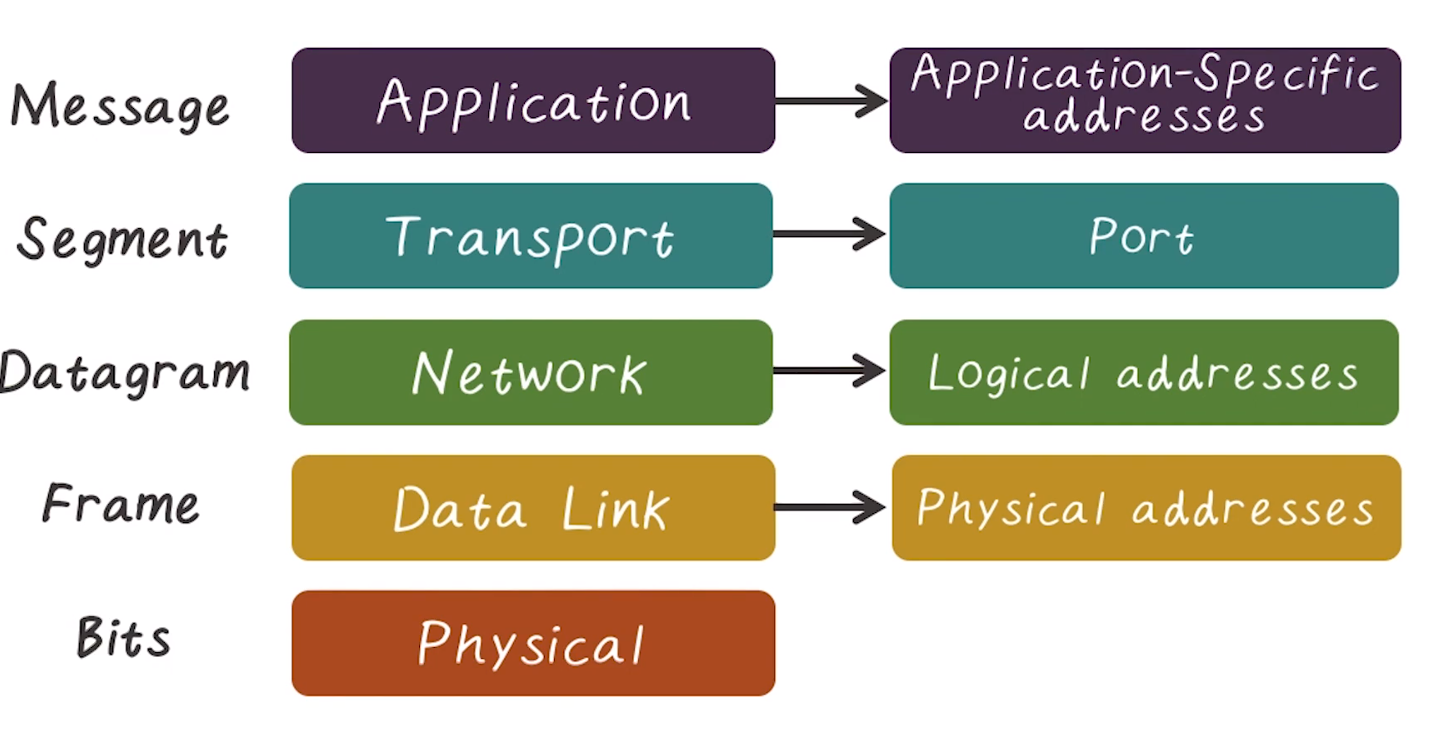
Addressing at each layer
Protocols at each layer
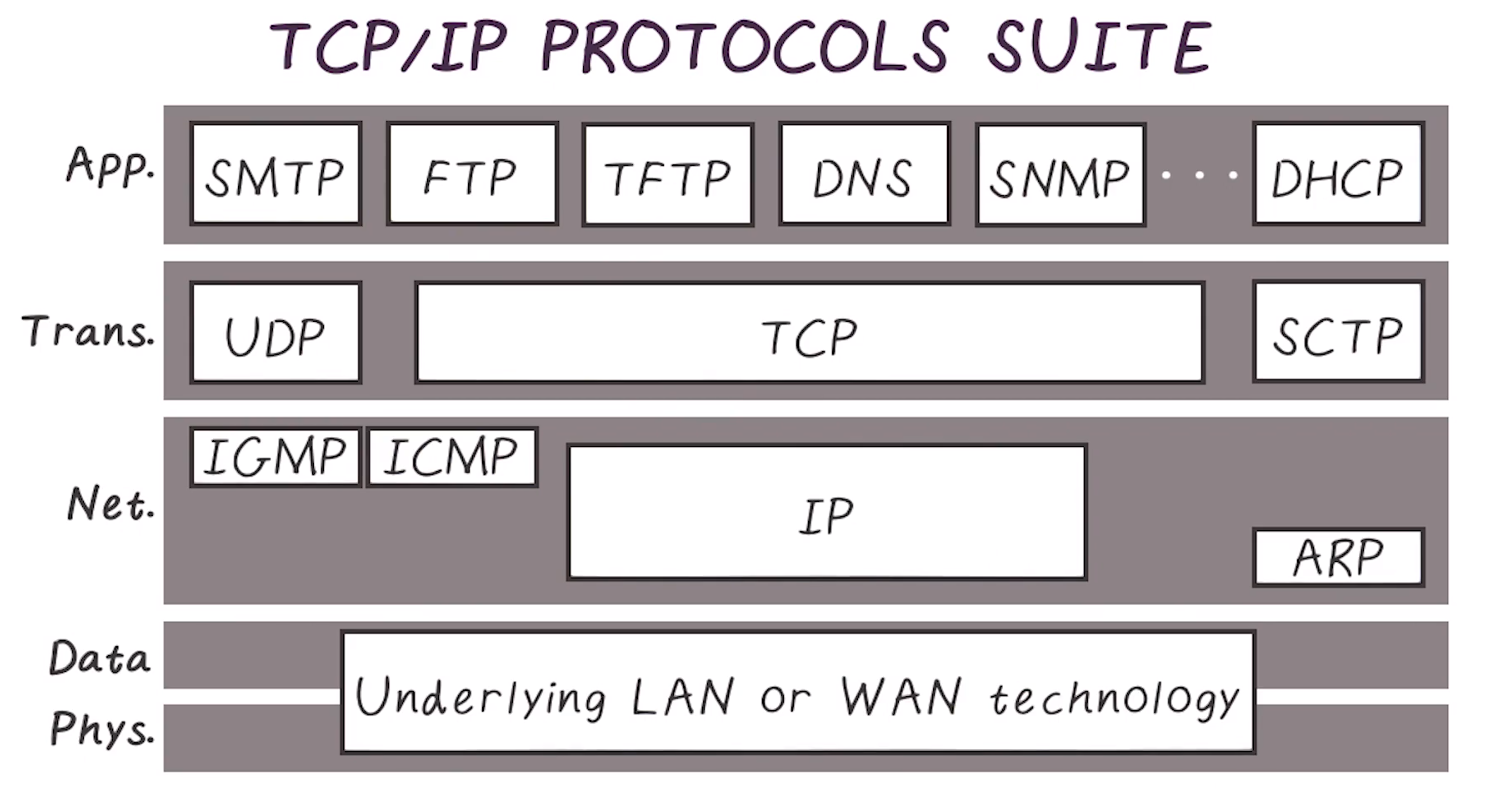
- Goes into TCP vs UDP in detail, discusses strengths and tradeoffs
- Addresses the Syn/SynAck/Ack three-way handshake
- Also mentions the Fin Active close equivalent
- Discusses some control flow stuff in TCP
Security
- CPS security goals are the same as traditional IT security, just harder to accomplish and higher stakes
- The security of a system/application/protocol is relative to:
- a set of desired properties
- an adversary with specific capabilities
- Goals are:
- Confidentiality
- Integrity
- Availability
Confidentiality
Tools for Confidentiality
- Encryption – transform information using a secret
- Access control – use rules and policies to limit access to information
- Authentication – determine identity of a role for someone requesting access
- Use something someone knows, has, or is
- Authorization – the determination if a person or system is allowed to access a resource, using a policy
- Physical security – the establishment of physical barriers to limit access to protected computational resources
- Authentication – determine identity of a role for someone requesting access
Integrity
- The property that information has not been altered in an unauthorized way
Availability
- The propety that information is accessible and modifiable in a timely fashion by those authorized to do so
Other Security Concepts
Assurance
- Refers to how trust is provided and managed in computer systems
- Policies specify behavioral expetations that people or systems have for themselves or others
- Permissions describe the behaviors that are allowed by the agents that interact with a person or system
- Protections describe mechanisms put in place to enforce permissions and policies
Authenticity
- The ability to determine that statements, policies, and permissions issued by persons or systems are genuine
- Digital signatures use cryptographic computations that allow a person or system to commit to the authenticity of their documents in a unique way that achieves nonrepudiation
Anonymity
- The property that certain records or transactions cannot be attributed to any individual
- Aggregation iss the combining of data from many individuals so that disclosed sums or averages cannot be tied to any individual
- Mixing is the intertwining of transactions, information, or communmications in a way that cannot be traced to any individual
- Proxies are trusted agents that are willing to engage in actions for an individual in a way that cannot be traced back to that person
- Psuedonyms are fictional identities that can fill in for real identities in communications and transactions, but are otherwise known only to a trusted entity
Threats and Attacks
Eavesdropping
- The interception of information inteded for someone else during its transmission over a communication channel
- Attack on confidentiality
Alteration
- The unauthorized modification of information
- Attack on integrity
Denial of Service
- The interruption or degradation of a data service or information access
- Attack on availability
Masquerading
- The fabrication of information that is purported to be from someone who is not actually the author
- Attack on authenticity
Repudiation
- The denial of a commitment or data receipt
- Attack on authenticity
Correlation and Traceback
- The integration of multiple data sources and information flows to determine the source of a particular data stream or piece of information
- Attacks on anonymity
Ten Security Principles
- Economy of mechanism
- complexity is the enemy of security. keep it simple
- Fail-safe defaults
- the default configuration should have a conservative protection scheme
- e.g. minimal access rights keeps user-level damage low
- Complete mediation
- every access to a resource must be checked for compliance
- things like caching permissions are scary
- Open design
- security should be publicly available for better scrutiny of security
- only secrets should be secret
- Separation of privilege
- multiple conditions should be required to get at protected things
- Least privilege
- what it says on the tin. compromise is kept cheaper if your lost password only gets at your stuff
- Least common mechanism
- if multiple users share a computer they should have separate accounts
- avoid sharing stuff wherever possible
- Psychological acceptability
- if security makes no sense or is hard or jarring, people will avoid using it
- Work factor
- keep in mind your threat model, scope security measures appropriately to avoid wasting resources you might need elsewhere
- Compromise recording
- sometimes it is more desirable to record details of an intrustion
- e.g., affording IP cameras is maybe better than a fleet of guards
Cryptographic concepts
Encryption
- a means to allow two parties, customarily called Alice and Bob, to establish confidential communication over an insecure channel that is subject to eavesdropping
Cryptosystem Characteristics
Can be described by:
- the set of possible plaintexts
- the set of possible ciphertexts
- the set of encryption keys
- the set of decryption keys
- the correspondence between encryption keys and decryption keys
- the encyrption algorithm to use
- the decryption algorithm to use
Symmetric Cryptosystems
- Alice and Bob share a secret key, which is used for both encryption and decryption
- key distribution requires each pari of communicating parties to share a separate secret key
- requires ((n * (n-1) )/ 2) keys
Public-Key Cryptography
- Uses public keys for encryption, private keys for decryption
- Only one key is needed for each recipient, with public and private components, n key pairs
- Can also be used to provide non-repudiation via signatures. Use a private key to sign/encrypt, anyone can then use public key to decrypt for confirmation
- Can also sign hash instead, slightly more secure
Cryptographic Hash Functions
- A compression function that maps an arbitrary-length file/input to a fixed-length hash/output
- To be considered “cryptographic” a hash function must have the following properties
- Must be “one-way”, e.g. it is simple to compute the hash given an input, but very difficult to get the input given only the hash
- Should be collision-resistant, meaning that it should be very difficult to find two inputs that give the same hash output
- Message authentication codes
- MAC enables data integrity, generated using hash function and a shared secret
- similar to salting password hashes
- recomputing hash with secret will show if file has been changed
Control Systems
- Controlling complex systems like the power grid
Introduction
- Understand and control segments of complex environments known as systems
- Room being heated system:
- Temperature gauge
- aka sensor
- Room being heated
- aka system or process
- furnace
- aka actuator
- thermostat
- aka controller
- Temperature gauge
- Foundation provided by linear systems theory
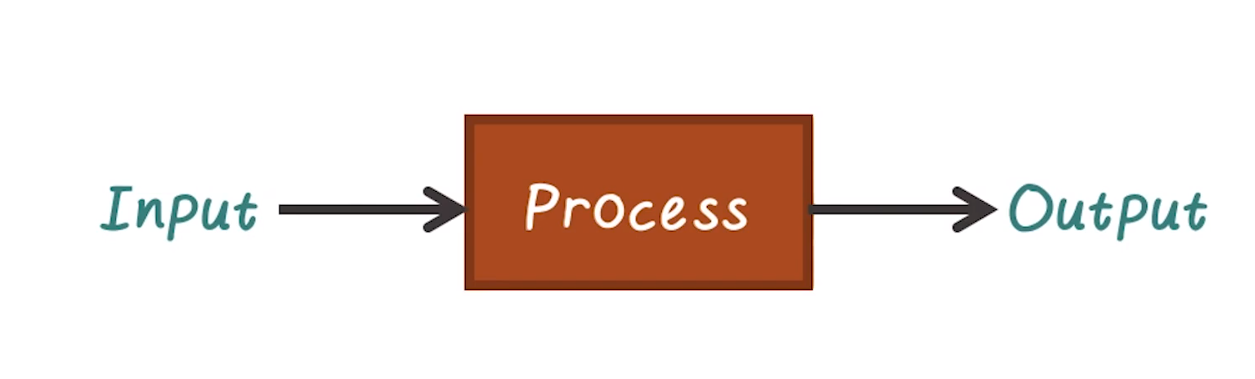
Open-Loop Conrol System
- Defined as a system without feedback
- e.g. a space heater
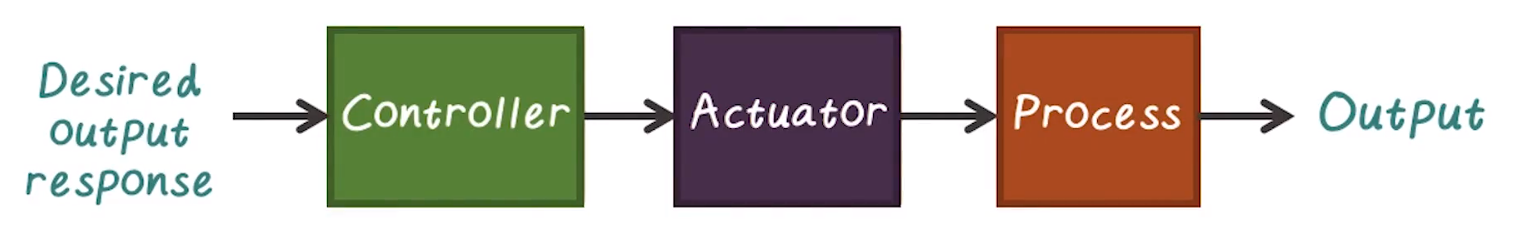
Closed-Loop Control System
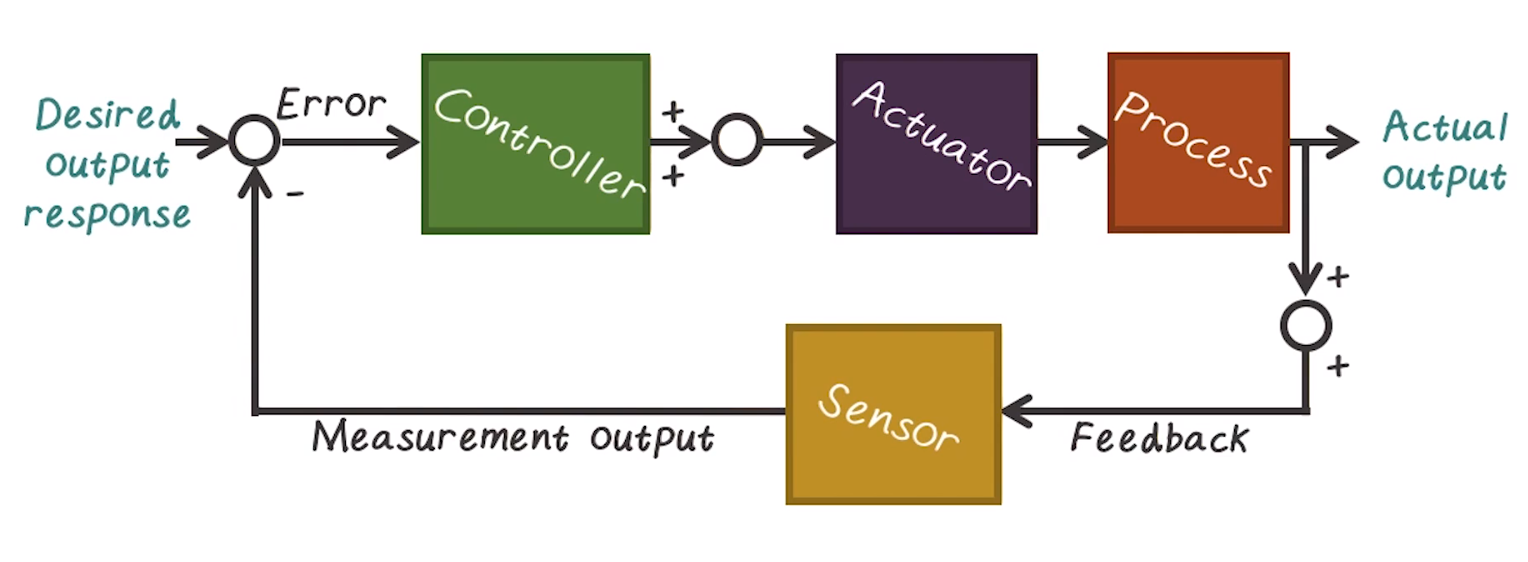
- In contrast, closed-loop system uses a measure to compare actual output with desired output
- e.g. home HVAC system instead of a space heater
- Many advantages over open-loop control
Multi-Loop Feedback Control System
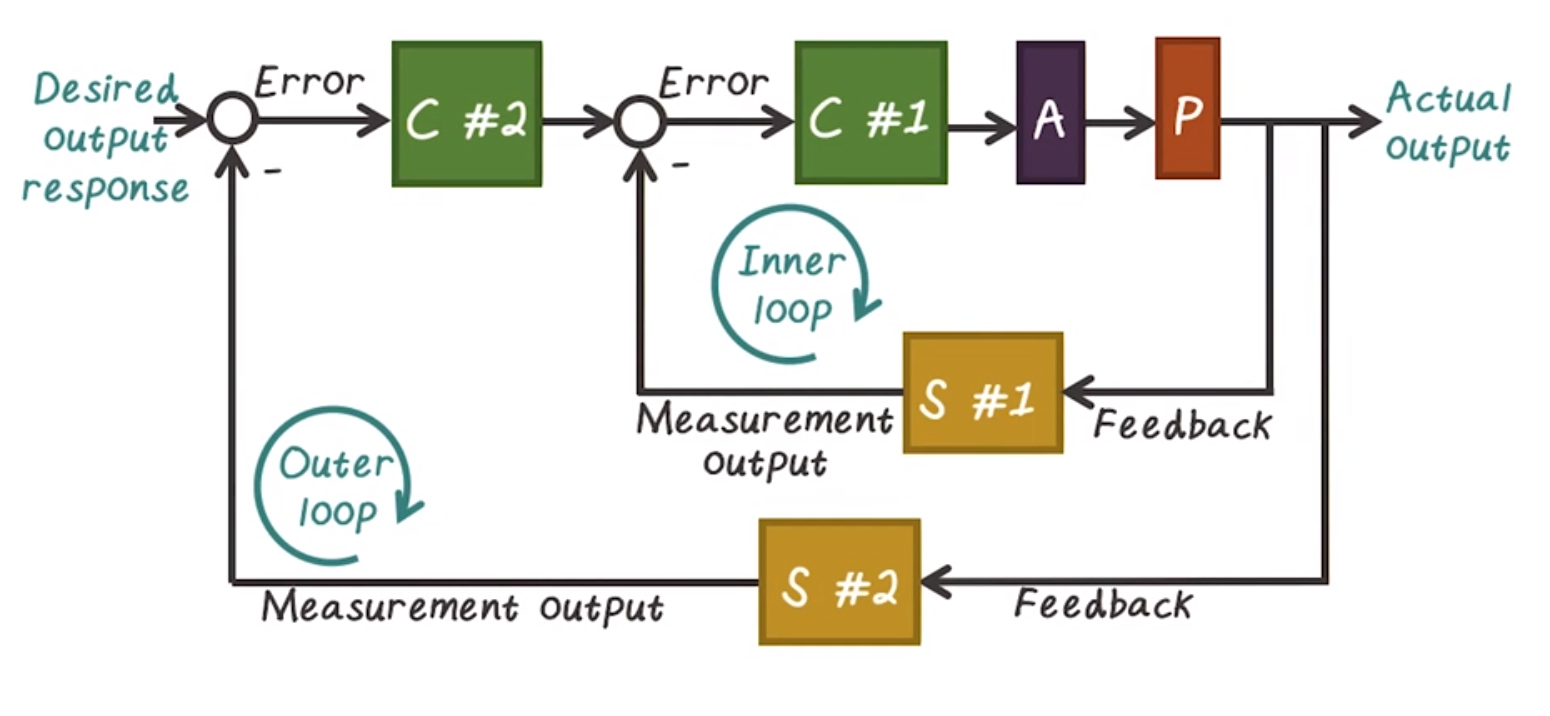
- Both inner and outer loops have controller and sensor
Multivariable Control System
- As systems become complex, multiple sensors and controllers must all be kept in the loop and their behavior monitored and adjusted
- e.g. humidity and pressure, in addition to temperature, for an HVAC system
Automation
- The control of an industrial process by automatic rather than manual means
- Necessary for complex systems
Productivity
- Defined here for our purposes as the ratio of physical output to physical input