ICPSS Lecture Notes - Lesson 6 - Introduction To Industrial Control Systems & Operations
Intro To Industrial Control Systems & Operations
System Assets
- Sensors
- Actuators
- Gauges
- Motor Drives
- Indicators
- PLCs
- RTUs
- IEDs
- HMIs
PLCs
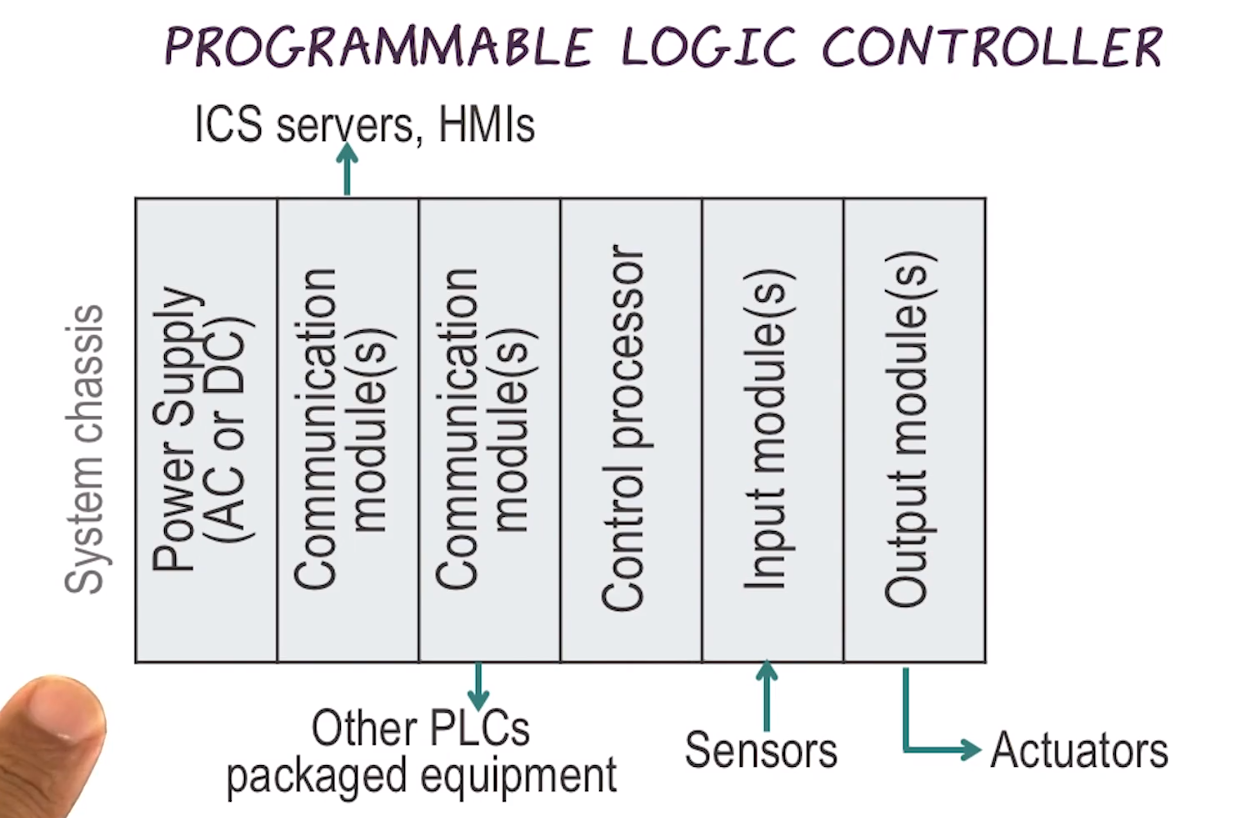
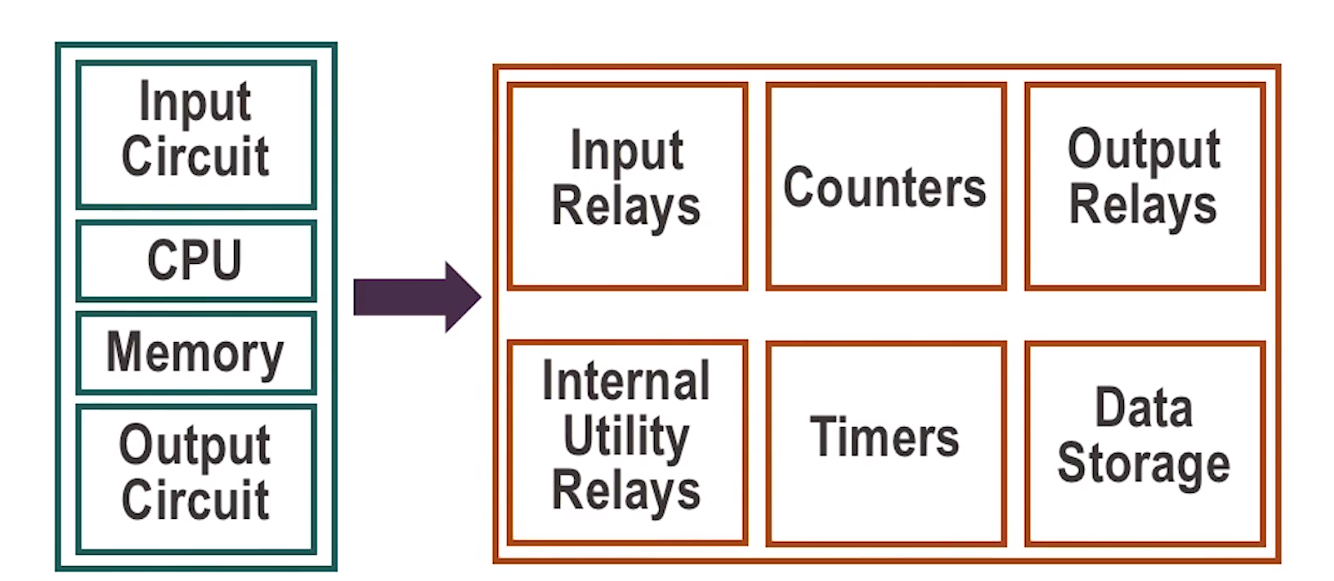
- Programmable Logic Controller
- A specialized industrial computer used for automation
- Unlike desktop computers, PLCs are typically physically hardened and may be specialized for specific industrial uses with multiple specailized inputs and outputs
- They do not usually have an OS. They usually rely on specific application programs that allow the PLC to function automatically, generating output actions
- They typically control real-time processes
PLC Operation
- Works by continuously scanning a program in a loop
- Check input status
- Execute program
- may be conditioned on inputs
- Update output status
PLC Ladder Logic
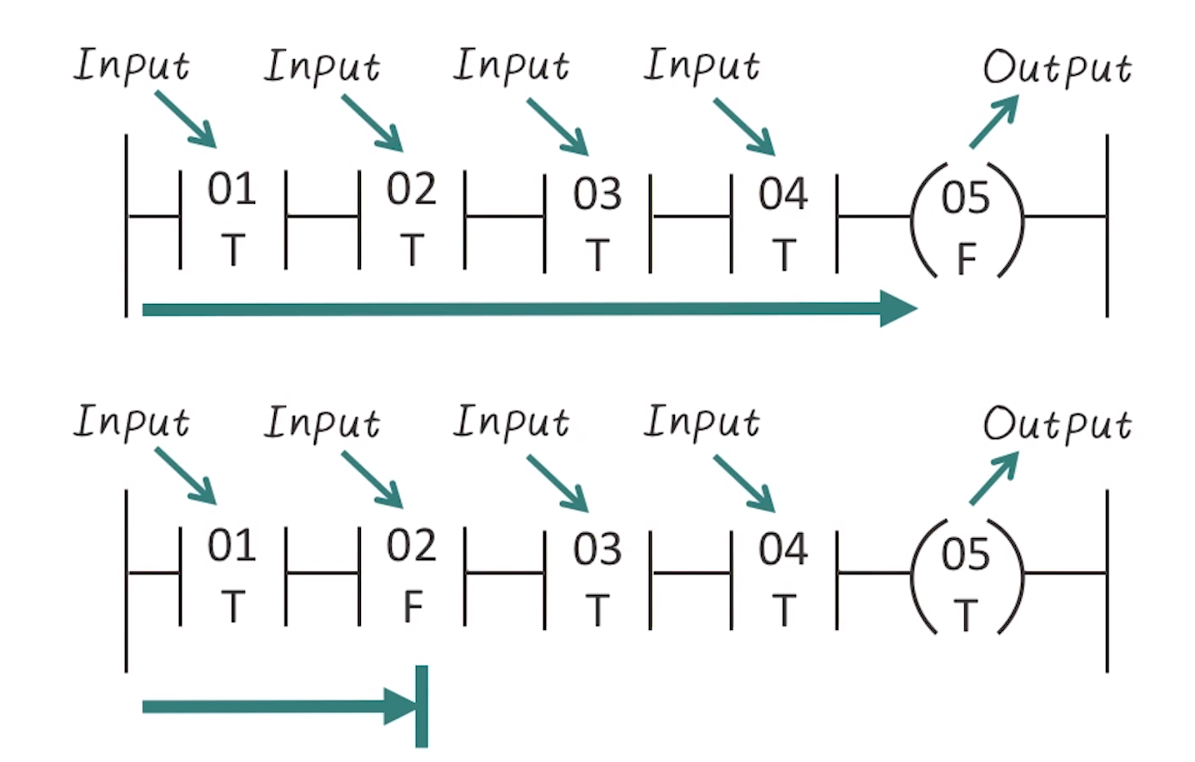
- PLC’s can use ladder logic, which is a simplistic programming language built into them (included in the relevant standard)
- LL gets its name from the legacy method of implementing discrete logic from electromechanical relays
- Can be thought of a series of connections between relay inputs (inputs) and relay coils (outputs)
- If output is reached, coil is energized
- Switched can be used to compare a continuous digital input to a binary physical input (comparing to setpoints)
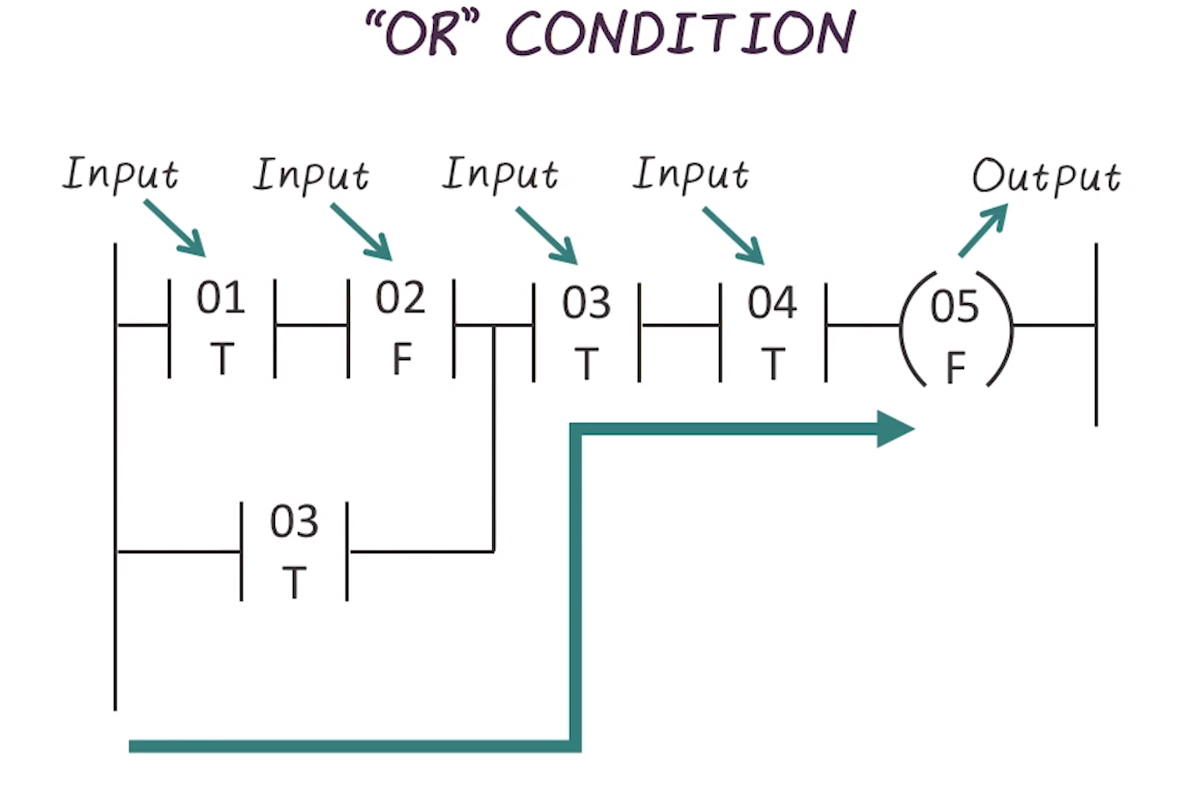
- logic can be more complex, see here an “or” condition
Other languages
- Standard includes ladder logic as mentioned above.
- Also includes:
- Structured Text (ST)
- Function Block Diagram (FBD)
- Instruction Lists (IL)
- Sequential Function Charts (SFC)
Remote Terminal Unit (RTU)
- Often reside in substation or otherwise remote location
- Monitor field parameters, and transmit back to monitoring station
- Usually include some way to beacon out, such as modem or radio
- Very limited bandwidth
- Thus, usually use minimalistic protocols such as “report by acception”
- Can be powered via solar or electric
- Often in extreme environmental conditions
- Modern RTUs overlap largely with PLCs, as tech advances
Intelligent Electronic Device (IED)
- Each industry has unique requirements, so equipment will vary from one to the next
- IEDs are used as bridge between analog and digital domains, used widely in power grids
- As with all tech, growing more sophisticated over time
- For this class, we can assume the IED supports a specific function within the overall control system, as opposed to RTU or PLC which are meant to be flexible enough for general use
Human-Machine Interface (HMI)
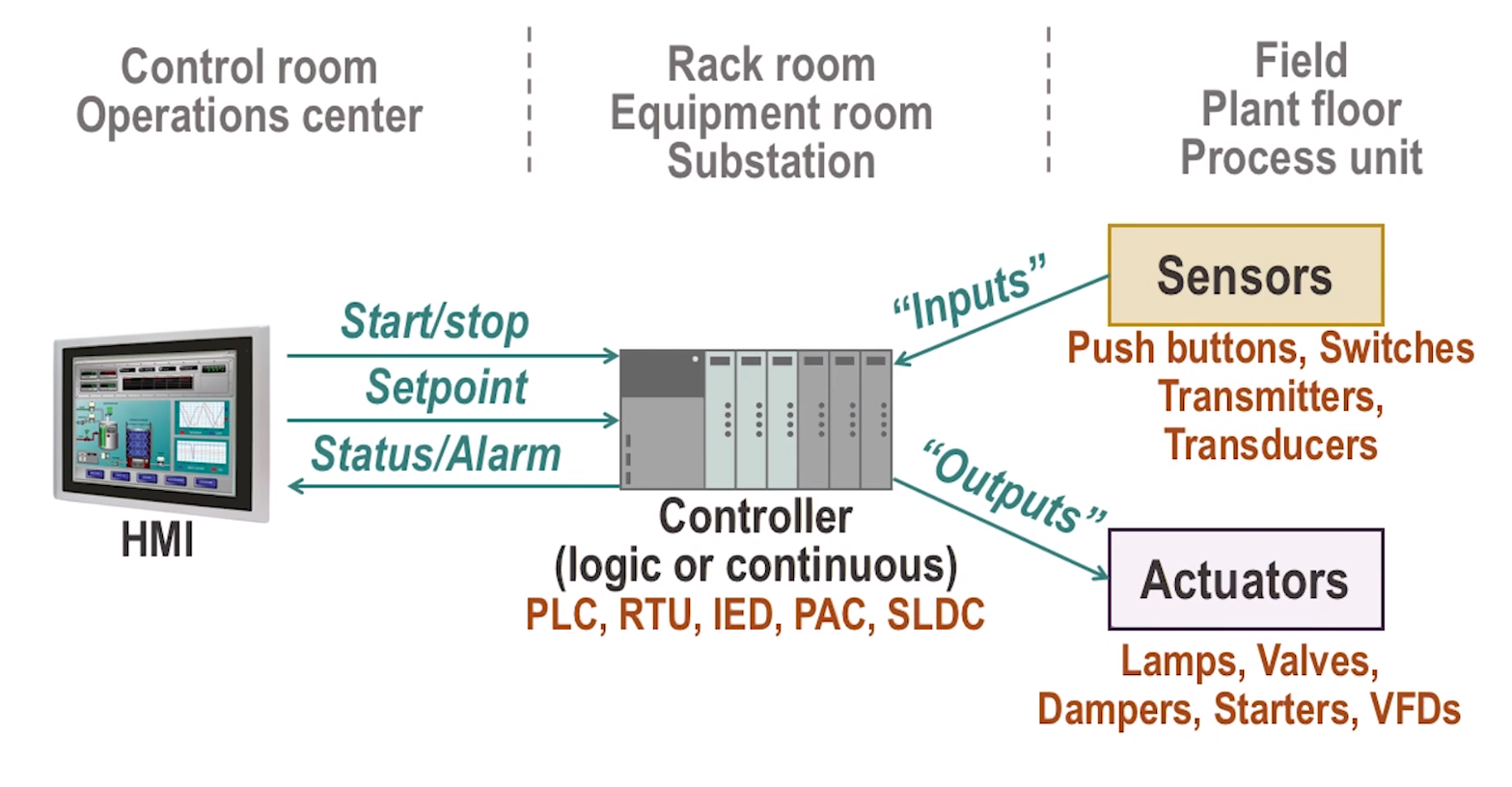
- Replace manual switches and dials with digital equivalents
- Much easier to adapt and adjust
- Can be run on either commodity hardware, or on industrial hardened machines with a touch panel
- Usually runs on Windows Embedded
- Allows “single pane of glass” control over complex processes
- Interesting note, usually no authentication to avoid password lockouts in emergencies
- Security is usually done at local workstation by restricting application execution, and also leans on physical security
Supervisory Workstations
- Read-only, strictly for monitoring use
- Can, however change parameters such as alarm limits or process setpoints
- HMI system or dashboard/workbook from data historian
Data Historian
- specialized software system that collects point values, alarm events, batch records, and other information from industrial devices or systems, and stores them in a purpose-built database
- There are some third-party vendors, but often these come from first party ICS vendors
- Data points referred to as ‘tags’ and can generally refer to anything
- Data often replicated across business and industrial networks
- This is a huge security concern, so historians must be hardened, and strict access controls put in place
Business Information Console
- Extensions of supervisory workstations
- Designed to deliver business intelligence to upper management
- Consist of same data obtained from HMI or data historian systems
- May be a physical console, or a historian with an ICS DMZ located elsewhere
Other Assets
- Printers
- Badge readers
- IP Telephones
- IP Cameras
- AD
- Time servers
- All of the above present attack surface and must be assessed
Control Loop
- Read data from sensors
- Execute logic against the data
- Write data to automation devices
- Go to 1
Closed vs Open Loops
- In closed loops, output of one iteration affects input of the next, while in open loop it does not
- Slides talk through example of ladder logic for cycling level in a water tank
- Slides talk through several examples around more complex control loops
Production Information Management
- All such processes and loops above must be managed from a central location, usually a data historian
- “Historizing” the data is the process of capturing and organizing the myriad data the control system generates
- From the historian, analytics are generated and used to inform the management of the system
- can be used to spot trend and anomalies, and optimize the process
Business Information Management
- Used to optimize for business KPIs
- Operational data in business network
- This reduces the strength of the security perimiter
- Each data access mechanism has security challenges
- Appropriate security mechanisms must be put in place
Process Management
- Driven by HMI
- HMI can be used to monitor output and adjust inputs or process setpoints
- HMI translates system functions to human-readable controls
- e.g. write single coil -> turn on water pump
- This means that compromising an HMI is a huge risk, as they functionally run the system
- e.g. Stuxnet
- However, attacker must have specific knowledge of the process in question to know which changes would actually have an impact
- This makes casual attacks harder, but is not a defense against targeted attacks
Safety-Instrumented Systems (SIS)
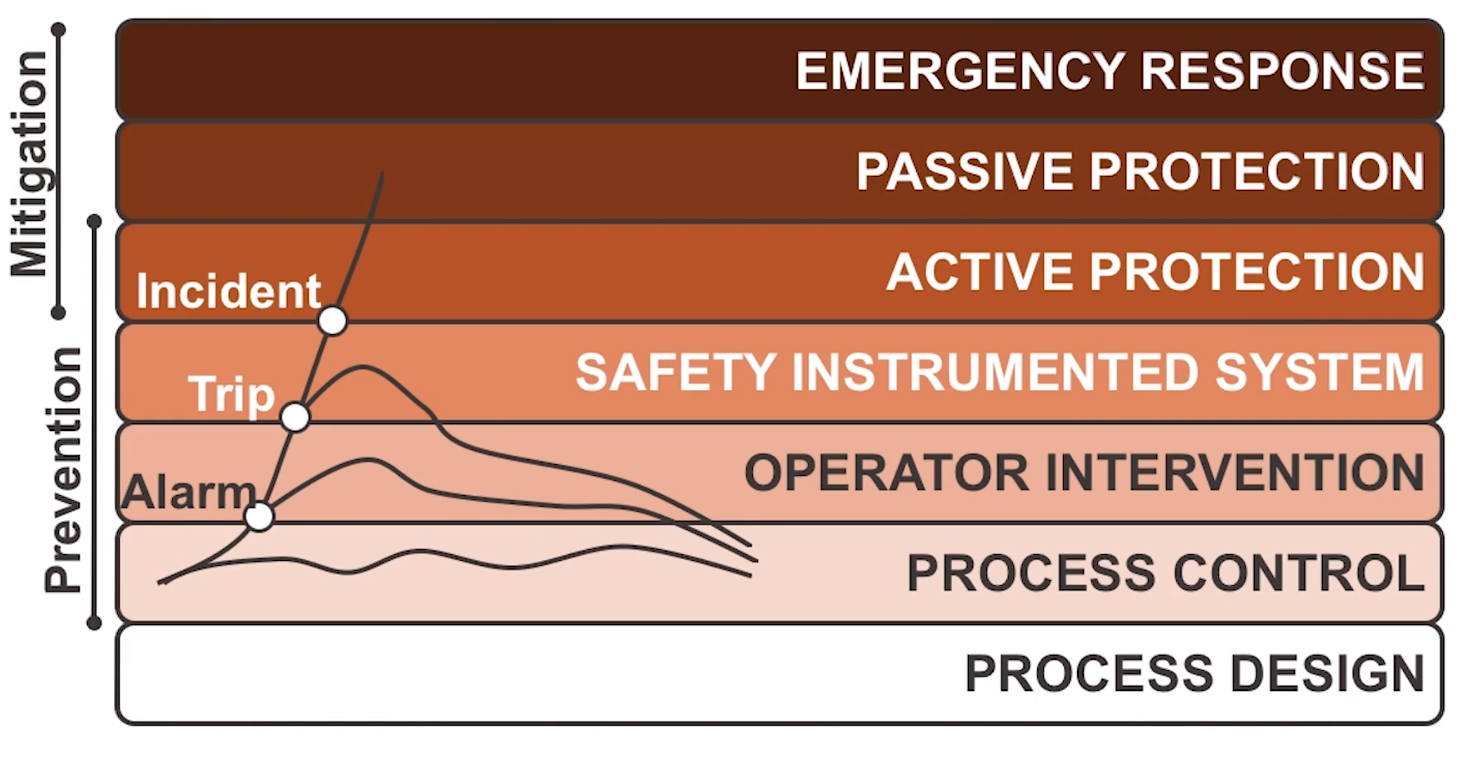
- Part of a layered stack of protections
- Helps as an automated safeguard before things become “incidents”
- If compromised, this safety is removed.
- Key part of a DoS attack
The Smart Grid
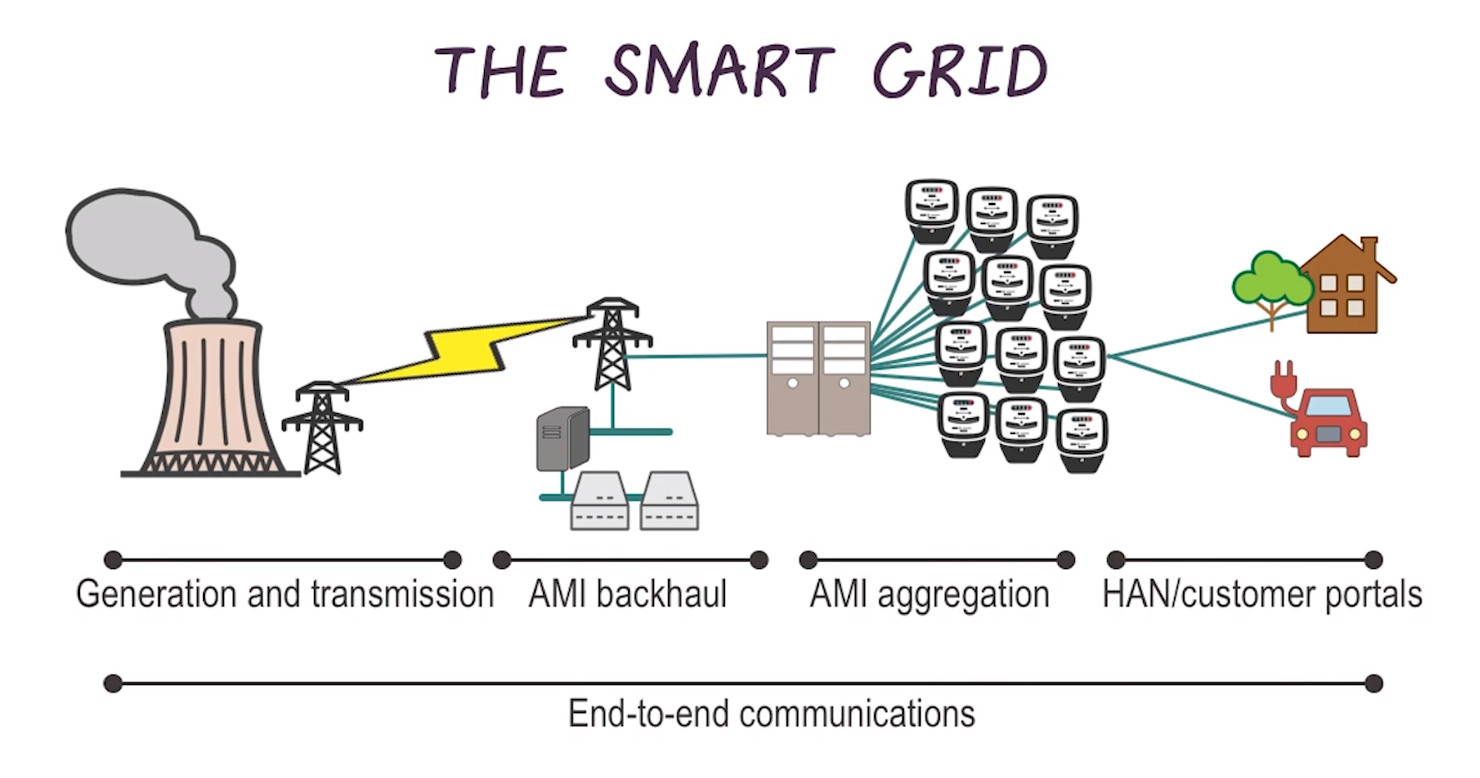
- An amalgamation of many industrial networks
- Built using the assets, processes, and controls discussed so far
- Because it’s such an amalgamation, attack surface is huge